Cryptography and PKI Terminology-Advanced
- Plain Text and Cipher Text
- Cipher
- One-Way Functions /Hashing
- Hashing Algorithms
- Collision
- Encryption & Decryption
- Symmetric Cryptography/Symmetric Key Encryption
- Symmetric Key Algorithms
- Asymmetric Encryption/ Asymmetric Cryptography/ Public Key Encryption
- Asymmetric Key Algorithms
- Digital Certificates
- Digital Signatures
- Hybrid Encryption
- Public Key Infrastructure (PKI)
- Keystore and Truststore
- SSL/TLS Handshake
Plain Text and Cipher Text
In the context of cryptography, Plaintext usually refers to readable simple text before it is encrypted into cipher text or readable text after it is decrypted.
Any message or a document or a file that is not encrypted is referred to as plaintext content.
- The input to a cryptosystem is plaintext, and the output is ciphertext. Algorithms in cryptography convert plaintext to ciphertext and viceversa. These respective processes are called encryption and decryption.
- It is crucial to protect plaintext held in computer files because unauthorized theft, disclosure, or transmission makes its contents fully visible and therefore possibly actionable. The storage medium, the device, its parts, and all backups must all be secured if they are to be stored.
Example:
We will encrypt a sentence using Caesar Cipher. The key is 7, which means the letter a becomes h.
Plaintext: hello world.
Ciphertext: olssv dvysk.
Like water and ice, plaintext and ciphertext can be transformed into the other and back without changing the essential elements of the usable form. But cleartext is another option, and it’s not always the same as plaintext.
Instead of storing or communicating sensitive data in plaintext, it is standard operating procedure to encrypt information before it is stored or transferred. The systems inside which plaintext is stored and the communication routes over which it travels are now acknowledged by data owners or custodians to be insecure. Therefore, it is preferable to manage data carefully, just as systems should be secured.
Cipher
Ciphers are used to hide the true meaning of a message. They use a variety of techniques to alter and/or rearrange the characters or bits of a message to achieve confidentiality. Ciphers convert messages from plaintext to ciphertext on a bit basis (that is, a single digit of a binary code), character basis (that is, a single character of an ASCII message), or block basis (i.e, a fixed-length segment of a message, usually expressed in number of bits).
Following are few Types of ciphers:
- Transposition ciphers :Transposition ciphers transform a plaintext message into a cipher text message by rearranging the letters using an encryption method. To recover the original message, the decryption method merely reverses the encryption transformation
- Substitution ciphers :In substitution ciphers, each character or bit of the plaintext message is swapped out for a new character using the encryption method.
- One-time pads: One-time pads are a type of substitution cipher that are incredibly strong. One-time pads substitute each letter in the plaintext message with a new alphabet. One-time pads have the tremendous benefit of being an impenetrable encryption method when applied properly. Alphabetic replacement does not follow a repeated pattern, making cryptanalysis pointless.
- However, in order to guarantee the integrity of the algorithm, a number of conditions must be met.
- The one-time pad needs to be produced at random. It would be possible for cryptanalysts to decipher the code if a word or passage from a book were used.
- Each one-time pad can only be utilized once. If pads are reused, cryptanalysts may be able to identify the key values used by comparing commonalities between many messages encrypted with the same pad.
- The one-time pad needs to be produced at random. It would be possible for cryptanalysts to decipher the code if a word or passage from a book were used.
- The encryption key’s length must be at least equal to the message’s length. This is so that just one character of the message can be encoded for each character of the key.
- However, in order to guarantee the integrity of the algorithm, a number of conditions must be met.
- Block Ciphers : Block ciphers work with “chunks,” or blocks, of a message and simultaneously apply the encryption algorithm to every block of the message. Block ciphers include the transposition ciphers. The straightforward challenge-response method takes a word as input and flips all of its letters. The more challenging columnar transposition cipher employs the transposition algorithm and a secret keyword to encrypt a complete message (or a portion of a message). The majority of contemporary encryption techniques use a block cipher of some kind.
- Stream Ciphers: A message (or data stream) is processed by stream ciphers one character or bit at a time. A stream cipher is exemplified by the Caesar cipher. Because the algorithm treats each letter of the plaintext message separately, the one-time pad is also a stream cipher. Block ciphers are a subset of stream ciphers that can be used in this way. In such activities, a buffer fills up with real-time data, which is then delivered to the receiver encrypted as a block.
One-Way Functions /Hashing
A one-way hash or Hashing is a function that takes a variable-length string (a message) and produces a fixed-length value called a hash value.
For example, if Bob wants to send a message to Alice and he wants to ensure the message does not get altered in an unauthorized fashion while it is being transmitted, he would calculate a hash value for the message and append it to the message itself. When Alice receives the message, she performs the same hashing function Bob used and then compares her result with the hash value sent with the message. If the two values are the same, Alice can be sure the message was not altered during transmission. If the two values are different, Alice knows the message was altered, either intentionally or unintentionally, and she discards the message.
Hashing is primarily used :
- To verify data integrity
- To provide authenticity.
- To store sensitive data.
A hash function is an algorithm that converts data of any size into an output of a specific size. The result is a hashed text known as a digest or a hash value. A cryptographic hash function’s primary goal is to confirm the validity of data.
Hashing Algorithms
Note that a hash algorithm or function is mainly used for comparison purposes and not for encryption.
Following are the properties of a hash function:
- Deterministic – The output should be the same for a given same input.
- Compression – The hash function’s output is much smaller than the input size.
- Not reversible – We can’t reverse a hash value back to the original password.
- Collision resistant – Two inputs do not result in the same output.
- Non-predictable – A hash function randomly generates a unique hash value that is not predictable.
Following are the few hashing algorithms.
MD5
One-way cryptographic hashing is done using the message digest 5 (MD5) technique. It produces a hash value or digest that is a 128-bit string. MD5 is frequently used to check the integrity of data.
Secure hashing algorithm – SHA
SHA was designed by National Security Agency and published by the NIST to be used with the Digital Signature Standard (DSS). SHA was designed to be used in digital signatures and was developed when a more secure hashing algorithm was required for U.S. government applications.
SHA output produces a 160-bit hash value, or message digest. This is then input into an asymmetric algorithm, which computes the signature for a message.
SHA and MD4 are comparable. It provides a 160-bit hash rather than a 128-bit hash and uses additional mathematical operations to make it more resilient against brute-force assaults, such as birthday attacks.
SHA was enhanced and given the new name SHA-1. Since it was recently discovered to be collision-prone, SHA-1 is no longer regarded as secure for applications requiring it. The SHA-256, SHA-384, and SHA-512 algorithms are updated versions of this one (together referred to as the SHA-2 and SHA-3 families). For all applications, the SHA-2 and SHA-3 families are regarded as secure.
Collision
The term “collision” refers to two inputs having the same hash value. It is straightforward to get to a collision with simple hash functions. Consider the scenario where the hash function h(text) adds up all the character codes in a text. For texts containing the same letters in a different order, it will generate the same hash value (collision), i.e. h(‘abc’) == h(‘cab’) == h(‘bca’). Cryptographers have created collision-resistant hash algorithms to prevent collisions.
Cryptographic hash functions are exceedingly unlikely to collide, hence it is thought that each input is virtually exclusively identified by its matching cryptographic hash. Additionally, it is quite difficult to locate an input message that hashes to a specific value.
One-way hash functions, which are impossible to invert, are used in cryptography. A strong cryptographic hash algorithm, like SHA-256, has very low probability of being cracked by brute force.
Let’s elaborate on this definition:
- Let’s assume that hash value h=hash(p) for certain strong cryptographic hash function hash.
- It is expected to be extremely hard to find an input p’, such that hash(p’)=h.
- Most modern strong cryptographic hash functions have no known collisions.
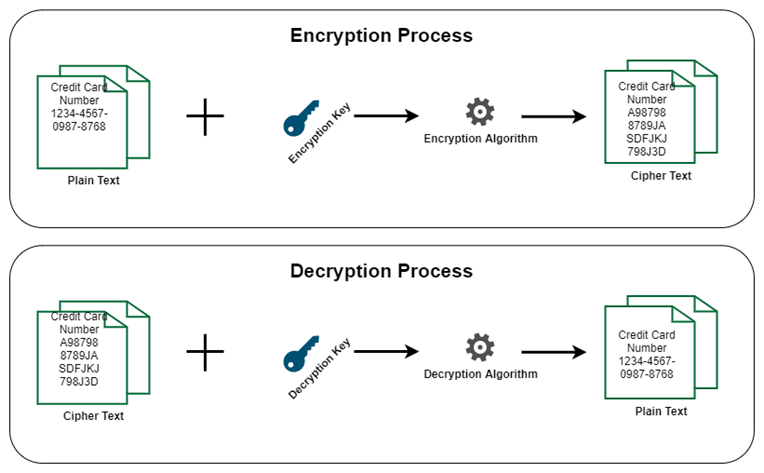
Encryption & Decryption
Encryption is a cryptographic operation which transforms the original information (plain text) into an unrecognizable form (cipher text). Whereas Decryption is the process of converting unrecognizable form of data (Ciphertext) back into its original form (plain text).
There are 3 major components to any encryption/decryption system:
- The data
- The encryption/decryption engine (Algorithms)
- Keys
Importance
In order to secure a wide range of information technology (IT) assets, encryption is crucial. It provides the following:
- Confidentiality encodes the message’s contents.
- Authentication provides the origin of a message.
- Integrity assures that the contents of a message have not been changed since it was sent.
- Nonrepudiation restricts senders from denying they sent the encrypted message.
Advantages of encryption and decryption
- Increases trust levels: Multiple parties can improve mutual confidence by utilizing encryption and decryption. Customers might be more inclined to utilize a website that uses data encryption for their personal information, for instance. Similar to this, it’s possible that two users only want the intended recipients to see a private communication that they exchange online, say over email.
- Data Protection during rest or in transit: Encryption is frequently used by websites and software programs to protect sensitive data at rest or during transit. To protect the user, a website might encrypt the credit card information entered by a user into an e-commerce business. Information like usernames, passwords, and credit card numbers are protected by using encryption.
Symmetric Cryptography/Symmetric Key Encryption
In symmetric cryptography (or symmetric-key encryption), the same key is used for both encryption and decryption.
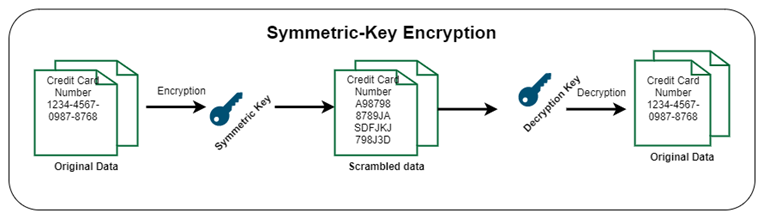
It means that to decrypt the scrambled data, one must have the same key that was used to encrypt it. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private communication link.
For n communicating entities, symmetric cryptography requires n(n-1)/2 keys.
Symmetric Key Cryptography is widely used in today’s Internet and primarily consists of two types of algorithms, Block and Stream.
Stream ciphers work on a single bit (byte or computer word) at a time and execute some form of feedback structure so that the key is repeatedly changing.
A block cipher is so-called because the scheme encrypts one block of information at a time utilizing the same key on each block.
Advantages of symmetric cryptography
- Inexpensive to produce a strong keys for ciphers
- The computational power required is less for symmetric cryptography
- Hard to break if using a large key size
Challenges/Weakness of symmetric cryptography
- Key exchange require secure mechanisms
- Each set of communication parties require a unique key
- Provides only confidentiality
Symmetric Key Algorithms
Today, symmetric algorithms come in a variety of forms. They use several techniques to offer encryption and decryption functionality. They are all symmetric methods, which means that the sender and receiver are utilizing two different copies of the same key.
Following are the popular symmetric key algorithms
- Data Encryption Standard (DES)
DES is a symmetric block encryption algorithm. When 64-bit blocks of plaintext is input, 64-bitblocks is the output. It uses a 64-bit key: 56 bits make up the real key, and 8 bits are used for parity.
When the DES algorithm is applied on data, it divides the message into blocks and operates on them one at a time. The blocks are put through 16 rounds of transposition and substitution functions. The key value used with the algorithm determines the kind, order, and order of the transposition and substitution functions. The output is a 64-bit blocks of cipher text.
Currently, the DES algorithm is broken and is not recommended to use.
- Triple-DES (3DES)
3DES uses 48 rounds in its computation, which makes it highly resistant to differential cryptanalysis. However, because of the extra work 3DES performs, there is a heavy performance hit. It can take up to three times longer than DES to perform encryption and decryption.
- Advanced Encryption Standard (AES)
The United States National Institute of Standards and Technology (NIST) developed the Advanced Encryption Standard (AES) as a specification for the encryption of electronic data in 2001. Despite being more difficult to build, AES is still commonly used because it is substantially stronger than DES and triple DES.
The features of AES are as follows −
- Symmetric key symmetric block cipher
- The key size can be 128/192/256 bits.
- Encrypts data in blocks of 128 bits each.
- Stronger and faster than Triple-DES
As a result, it generates 128 bits of encrypted cipher text as output from 128 bits of input. AES operates utilizing a chain of linked operations that replace and shuffle the input data, which is known as the substitution-permutation network principle.
AES performs well when implemented in hardware and software in a variety of products and settings. It requires little memory and is designed to be easily resistant against timing attacks.
- International Data Encryption Algorithm (IDEA)
IDEA was designed by James Massey of ETH, a research university in Zurich, Switzerland, and is generally considered to be secure.
(IDEA) is a block cipher and operates on 64-bit blocks of data. The 64-bit data block is divided into 16 smaller blocks, and each has eight rounds of mathematical functions performed on it. The key is 128 bits long, IDEA is faster than DES when implemented in software.
This algorithm offers different modes of operation similar to the modes as DES algorithm, but it is considered harder to break than DES because of its longer key size. IDEA is used in PGP and other encryption software implementations. It was thought that it would replace DES, but it is patented, which means that licensing fees would have to be paid to use it.
- Blowfish
Blowfish is a block cipher that works on 64-bit blocks of data. The key length can be anywhere from 32 bits up to 448 bits, and the data blocks go through 16 rounds of cryptographic functions.
It was intended to provide a fast, free, drop-in alternative to the aging Data Encryption Standard (DES) and International Data Encryption Algorithm (IDEA) encryption algorithms.
Blowfish is unpatented, substantially faster than DES and IDEA, and freely accessible for all purposes. However, because of its short block size, which is seen as insecure, it couldn’t totally replace DES.
- RC4, RC5, and RC6
RC4 was developed by Ron Rivest in 1987 and was considered a trade
secret of RSA Data Security, Inc., until it was leaked.
RC4 is one of the most commonly implemented stream ciphers. It has a variable key size, is used in the Secure Sockets Layer (SSL) protocol, and was (improperly) implemented in the 802.11 WEP protocol standard.
The algorithm’s popularity can be attributed to its simplicity, speed, and efficiency. However, it is susceptible to modification attacks. One reason for this was the switch from the RC method to the AES algorithm in IEEE 802.11i.
For its block size, key size, and number of rounds, the block cipher RC5 can use a number of different settings. Ron Rivest was the author of it. This algorithm uses blocks of 32, 64, or 128 bits, and its maximum key size is 2,048 bits. Additionally variable is the number of encryption and decryption rounds. Up to 255 rounds may be played.
Because RC6 is a block cipher that was developed from RC5, it has all of RC5’s characteristics. It was intended for the method to be submitted as AES, but Rijndael was used instead. The RC5 algorithm underwent minor changes to improve speed overall, yielding the RC6 algorithm.
Asymmetric Encryption/ Asymmetric Cryptography/ Public Key Encryption
In a symmetric key cryptography mechanism, a single secret key is used between two communicating entities, whereas in public key systems, each entity has different keys, known as asymmetric keys.
The two different asymmetric keys are mathematically related. When one key encrypts a message, the other key is needed to decrypt the message.
One public key and one private key make up the pair of keys in a public key system. The private key can only be used by the owner and the public key can be known by anybody.
Often, public keys are available for everyone to use.
The public and private keys are related mathematically, and if someone gets another person’s public key, he/she should not be able to figure out the related private key.
Which means that if an eavesdropper gets a copy of Bob’s public key, he/she can’t employ some mathematical analysis and find out Bob’s private key.
The important key is the private key, which should be protected strongly.
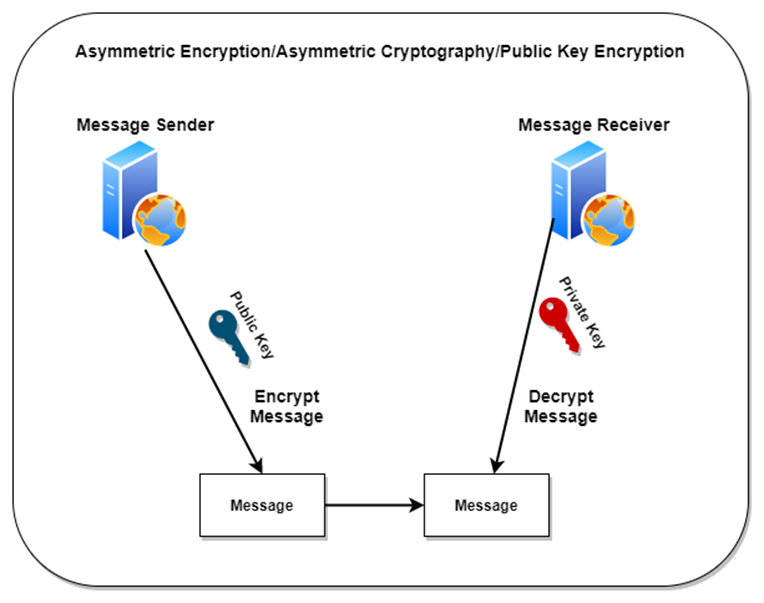
Advantages of Asymmetric key Cryptography:
• Ease of key distribution\exchange compared to symmetric systems.
• Easily scalable for large set of communicating entities compared to symmetric systems
• Provides authenticity and nonrepudiation.
Disadvantage of Asymmetric key Cryptography:
- Encryption process slower compared with symmetric systems
Asymmetric Key Algorithms
The following are examples of asymmetric key algorithms:
- Rivest-Shamir-Adleman (RSA)
The most well-known asymmetric algorithm is the public key RSA algorithm, which was created by Ron Rivest, Adi Shamir, and Leonard Adleman. Digital signatures, key exchange, and encryption may all be done using RSA, which is a de facto standard used all over the world. It was created in 1978 at MIT and offers both key encryption and authentication.
This algorithm’s security stems on how challenging it is to factor huge numbers back into their original prime numbers. The essential operation to convert a message from ciphertext to plaintext using a private key is analogous to factoring a product into two prime numbers. The public and private keys are functions of a pair of huge prime numbers.
The ability to employ RSA for both encryption and digital signatures is a benefit. RSA performs encryption and signature verification using its one-way function, and performs decryption and signature generation in the opposite direction.
It can be used as a key exchange protocol, in which case the symmetric key is encrypted before being sent safely to its destination. The symmetric algorithm DES, which is quickly being supplanted by AES, has been the most widely used with RSA. Therefore, a cryptosystem creates a symmetric key by utilizing either the DES or AES algorithm when RSA is employed as a key exchange protocol. The symmetric key is then sent to the recipient after being encrypted using their public key by the system. The symmetric key is secured since it can only be decrypted and extracted by the person who has the associated private key.
- Digital Signature Algorithm (DSA)
Digital Signature Algorithm is a FIPS (Federal Information Processing Standard) for digital signatures. It was proposed in 1991 and globally standardized in 1994 by the National Institute of Standards and Technology (NIST). It operates within the framework of modular exponentiation and discrete logarithmic problems, which are challenging to compute using a force-brute technique.
Benefits:
- Message Authenticity: Using DSA one can verify the origin of the sender using the right key combination.
- Integrity Verification: Anyone can’t tamper with the message since it will prevent the bundle from being decrypted altogether.
- Non-repudiation: The sender cannot claim they never sent the message if verifies the signature.
- Elliptic curve cryptosystem (ECC)
Elliptical curve cryptography (ECC), a public key encryption method founded on elliptic curve theory, it can be used to produce cryptographic keys more quickly, more efficiently, and in smaller sizes.
ECC is a substitute for the Rivest-Shamir-Adleman (RSA) cryptographic algorithm and is most frequently used for one-way email, data, and software encryption as well as digital signatures in cryptocurrencies like Bitcoin and Ethereum.
An elliptic curve is not an oval shape, but rather a looping line that intersects two axes, or lines on a graph that show where a point is located. Along the graph’s x-axis, the curve is perfectly symmetrical, or mirrored.
Systems that use public key cryptography, like ECC, combine two different keys through a mathematical procedure, which is then used to encrypt and decrypt data. One is a private key that is only known by the sender and recipient of the data, while the other is a public key that is known to everyone.
As opposed to the conventional method of generation as the product of big prime numbers, ECC creates keys through the characteristics of an elliptic curve equation.
- El Gamal
El Gamal is a public key algorithm that can be applied to key exchange, digital signatures, and encryption. It is based on computing discrete logarithms in a limited field, not on the difficulty of factoring huge integers. The power to which we must increase a given integer in order to obtain another given integer is known as a discrete logarithm. In other words, k is the logarithm in the equation bk=g if b and g are both integers. It is exceedingly challenging to calculate the logarithm when the numbers are large. Indeed, we are unaware of any effective technique to accomplish this with contemporary technology. Discrete logarithms are helpful in cryptography because of this. Actually, El Gamal is a Diffie-Hellman algorithm expansion. El Gamal’s biggest flaw is performance, even though it offers some of the same capabilities as some of the other asymmetric algorithms.
- Diffie-Hellman
A mutual secret can be established between two parties communicating over a public channel using the Diffie-Hellman (DH) Algorithm without having to send it over the Internet. DH enables the two to employ symmetric cryptography to encrypt and decrypt their communication or data using a public key.
Diffie-Helman is typically explained by two sample persons starting a conversation, Alice and Bob. Each person wants to communicate a secret piece of knowledge with the other. They decide on a piece of benign public information that will be blended with their privileged information and transmitted across an insecure channel in order to do this. As people communicate secrets, the information they desire to disclose is mingled with the common secret. Their secrets are blended with the public knowledge, or public key. They can extract the information that is publicly available as they decrypt the other person’s communication, and by knowing their own secret, they can infer the new information that was conveyed along with it. Although the description of this method makes it look simple, decryption by an outsider attempting to eavesdrop is theoretically impossible even with a lot of resources when large number strings are used for the private and public keys.
One of the earliest applications of asymmetric encryption or public-key cryptography (PKC) in practice is DH. Martin Hellman and Whitfield Diffie released it in 1976. Ralph Merkle and researchers from the British intelligence agencies are two more people who are credited with helping to develop DH (about 1969).
Digital Certificates
A digital certificate, which authenticates the identity of a website, person, group, organization, user, device, or server, is an electronic file linked to a pair of cryptographic keys. It is also referred to as an identity certificate or a public key certificate. The subject, which is the identity component, and a digital signature are both present on the certificate.
A website, person, group, organization, thing, user, or server’s identity and safe encryption are both guaranteed by digital certificates. They serve as the cornerstone for putting Public Key Infrastructure (PKI) security into practice.
Digital certificates can be used to secure a variety of things, including emails, devices, web servers, signatures, programs, and more. Digital certificates can also be used to encrypt data, enable HTTPS in the URL bar, verify the legality of a website, comply with PCI rules, boost website SEO ranks, and solidify a brand’s identity.
Digital Signatures
A digital signature is a hash of a message that uniquely identifies the sender of the message and proves the message hasn’t changed since transmission.
Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages. They are used to bind signatory to the message.
Similarly, a digital signature is a technique that binds a person/entity to the digital data. This binding can be independently verified by receiver as well as any third party.
Digital signature is a cryptographic value that is calculated from the data and a secret key known only by the signer.
Importance of Digital Signatures
Message authentication – When the verifier confirms the digital signature using the sender’s public key, he is confident that the signature has only been created by the sender and no one else.
Data Integrity – The digital signature verification at the receiver end is invalidated if an attacker gains access to the data and modifies it. The output of the verification procedure will not match the hash of the updated data. Therefore, presuming that data integrity has been compromised, the receiver can safely reject the message.
Non-repudiation – The signer can only produce an original signature on the given data because it is presumed that only he or she knows the signature key. As a result, if a dispute ever occurs, the receiver can show data and the digital signature to a third party as proof.
Hybrid Encryption
An application of cryptography that combines two or more encryption algorithms, particularly a combination of symmetric and asymmetric encryption. Hybrid encryption is a method of encoding and decoding data that combines the efficiency of a private symmetric encryption scheme with the speed and convenience of a public asymmetric encryption technique is known as hybrid encryption.
Public Key Infrastructure (PKI)
A PKI (public key infrastructure) uses a public and private cryptographic key pair that is acquired and exchanged through a trusted authority to allow users of a generally unsecure public network, like the Internet, to safely and discreetly exchange data and money. Digital certificates that can be used to identify a person or an organization are provided by the public key infrastructure, along with directory services that can store and, if required, revoke the certificates.
Public key assurance is provided by PKI. It offers public key distribution and key identification. The following parts make up the ecosystem of PKI.
1. Public Key Certificate or popularly known as Digital certificates
Digital certificates are like the ID cards such as passports, driving license issued to persons to prove their identity.
A digital certificate does the same basic thing in the electronic world, but with one difference. Digital Certificates are not only issued to people but they can be issued to computers, software packages or anything else that need to prove the identity in the electronic world.
The Certification Authority (CA) stores the user client’s public key in digital certificates together with other pertinent data like the client’s details, the expiration date, the usage, the issuer, etc.
2. Private Keys
While a client’s associated secret private key can be kept on the key owner’s computer, the client’s public key is kept on the certificate. In general, this approach is not used. An attacker can simply access the private key if he has access to the machine. Because of this, a private key is kept on a secure portable storage token that requires a password to access.
For storing private keys, manufacturers frequently employ various proprietary storage formats. For instance, Verisign, GlobalSign, and Baltimore employ the common.p12 format, whereas Entrust uses the proprietary.epf format.
3. Certification Authority (CA)
CA provides a client with a certificate and helps other users validate the certificate. The CA is in charge of accurately verifying the identity of the client requesting a certificate, as well as checking that the certificate’s contents are accurate and digitally signing it.
- Registration Authority.
CA may make use of a third-party Registration Authority (RA) to carry out the required identification verifications on the individual or business requesting the certificate. Although the RA might pose as a CA to the client, they do not really sign the certificate that is issued.
- Certificate Management System
The certificate management system publishes, suspends temporarily or permanently, renew, or cancel certificates. Normally, certificate management systems don’t remove certificates since it might be necessary to later verify their legitimacy, possibly for legal reasons. Running certificate management systems allows a CA and any connected RA to keep track of their obligations and liabilities.
Keystore and Truststore
In cryptography, Keystores and Truststores are repositories that contain cryptographic artifacts like certificates and private keys that are used for cryptographic protocols such as TLS.
Often, a Keystore contains personal certificates, plus the corresponding private keys that are used to identify the owner of the certificate.
A Truststore usually contains the signer certificates (also known as certificate authority certificates) which the endpoint/system trusts.
Typical characteristics of a keystore:
- Security: A Keystore is meant to be a safe place to keep certificates and cryptographic keys. It offers defense against illegal entry, tampering, and theft of private information.
- Encryption: To prevent unwanted access, a key store can be encrypted with a password or other authentication method. This guarantees the security of the keys and certificates kept in the Keystore.
- Key management: A Keystore provides facilities for managing keys and certificates, such as generating new keys, revoking old keys, and managing certificates.
- Portability: A Keystore can be exported and imported to different systems and applications. This makes it possible to use the same keys and certificates across different environments.
- Flexibility: A keystore can store different types of keys and certificates, such as public keys, private keys, and X.509 certificates.
- Standards-based: Keystores are based on industry-standard cryptographic protocols and algorithms, such as PKCS#12 and JKS.
- Integration: Keystores can be integrated with different types of applications, such as web servers, email clients, and mobile applications. This makes it possible to use the same keys and certificates across different types of applications.
Typical characteristics of a Trust store:
- Repository of trusted certificates: A Truststore is a repository of trusted digital certificates that are used to establish a secure connection between two parties over a network.
- Contains certificates issued by trusted CAs: The Truststore contains digital certificates issued by trusted Certificate Authorities (CAs) that are authorized to issue digital certificates.
- Public key cryptography: The Truststore uses public key cryptography to verify the identity of a remote party by verifying the digital signature of the presented certificate.
- Can be modified: The Truststore can be modified to add or remove trusted certificates using the keytool utility provided by Java.
- Used in SSL/TLS: The Truststore is commonly used in Java to establish a secure connection over the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols.
- Security measure: Using a Truststore is a critical security measure for Java programs that communicate over a network as it helps prevent security threats such as man-in-the-middle attacks.
SSL/TLS Handshake
A Secure Sockets Layer (SSL) / Transport Layer Security (TLS) handshake is the process of creating a safe and secure encrypted communication channel between the client (typically a user’s browser) and the server (web server). Hence, protecting user information and ensuring risk-free transactions by preventing any man-in-the-middle (any attacker) from reading or changing the actual data.
This process typically happens before the actual transfer of data. The browser and the web server will first authenticate each other and build a secure encrypted communication channel using SSL/TLS handshake.
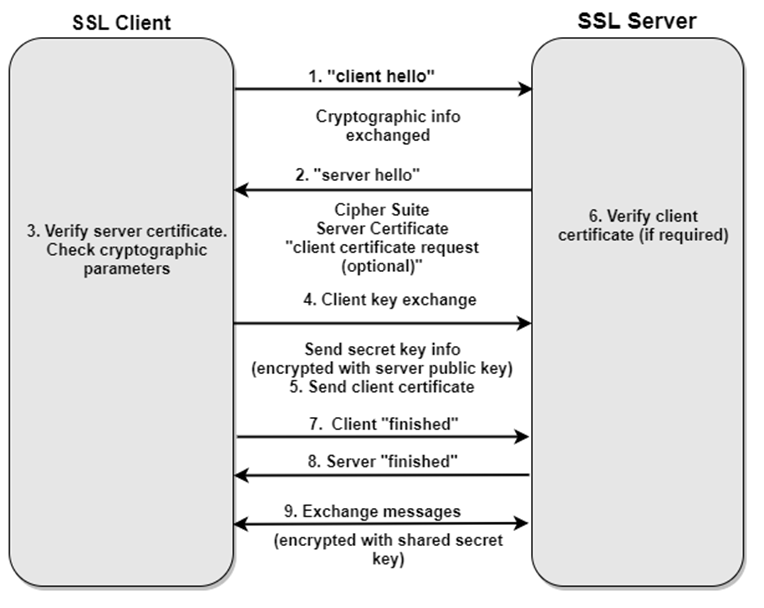
SSL/TLS Handshake in brief
The SSL/TLS handshake requires multiple exchanges between the client and the server in order to perform secure communication
- Agree on the (TLS 1.0, 1.2, 1.3, etc.) version.
- Agree on the cipher suite.
- Verify each other by exchanging digital certificates.
- Create session keys to use symmetric encryption after the handshake is complete.
Also Read: Terminology-Basic, Terminology-Intermediate, Security Terminology Section
Suggested Exercises: Cryptography Tests
